Featured
Table of Contents
- – What Is A Vpn & How Does It Work?
- – A Guide To Vpn: What Is Virtual Private Networ...
- – [Solved] What Does Vpn Stands For?
- – What Is A Vpn? How Does It Work And Why Do Yo...
- – Vpn Connection: What Is It And Why Do You Nee...
- – What Is Ssl Vpn?
- – What Is Vpn? - Understanding Virtual Private...
- – Vpn Full Form
- – Vpn - Definition By Acronymfinder
- – What Is A Vpn? An Introduction To Virtual Pr...
- – What Does Vpn Stand For? Are You Using Vpn? ...
What Is A Vpn & How Does It Work?
Anybody on the same network will not be able to see what a VPN user is doing. This makes VPNs a go-to tool for online personal privacy.
The VPN customer is not visible to the end user unless it produces performance issues. By utilizing a VPN tunnel, a user's gadget will connect to another network, hiding its IP address and securing the data. This is what will hide private information from enemies or others wanting to access to an individual's activities.
VPNs associate a user's search history with the VPN server's IP address. VPN services will have servers situated in various geographical areas, so it will appear like the user might be from any among those locations. VPNs can impact performance in numerous methods, like the speed of users' internet connections, the procedure types a VPN company can utilize and the type of file encryption used.
A Guide To Vpn: What Is Virtual Private Network? - Zenarmor
A kill switch is a last hope security feature in some VPN items. If the VPN connection is interfered with, the kill switch will immediately disconnect the gadget from the web to remove the opportunity of IP address direct exposure. There are 2 types of kill switches: prevent devices from connecting to hazardous networks when the device is linked to the VPN.
are more protected. They keep the gadget from connecting to non-VPN connections even while detached from the VPN server. VPNs are utilized for virtual privacy by both normal internet users and organizations. Organizations can use VPNs to make sure outdoors users that access their information center are licensed and utilizing encrypted channels.
When surfing the web, an internet user could have info accessed by an assailant, consisting of searching routines or IP address. If privacy is a concern, a VPN can provide users with assurance. Encryption, anonymity and the ability to navigate geographically blocked material is what most users find important in a VPN.
[Solved] What Does Vpn Stands For?
The difficulties of utilizing a VPN, however, include the following: Not all gadgets might support a VPN. VPNs do not safeguard versus every hazard. Paid VPNs are more relied on, protected choices. A VPN may decrease web speeds. Anonymity through VPNs has some s restrictions-- for example, browser fingerprinting can still be done.
Network administrators have a number of choices when it concerns deploying a VPN that consist of the following. Remote gain access to customers connect to a VPN entrance server on the organization's network. The entrance requires the device to authenticate its identity before granting access to internal network resources. This type normally depends on either IPsec or SSL to protect the connection.
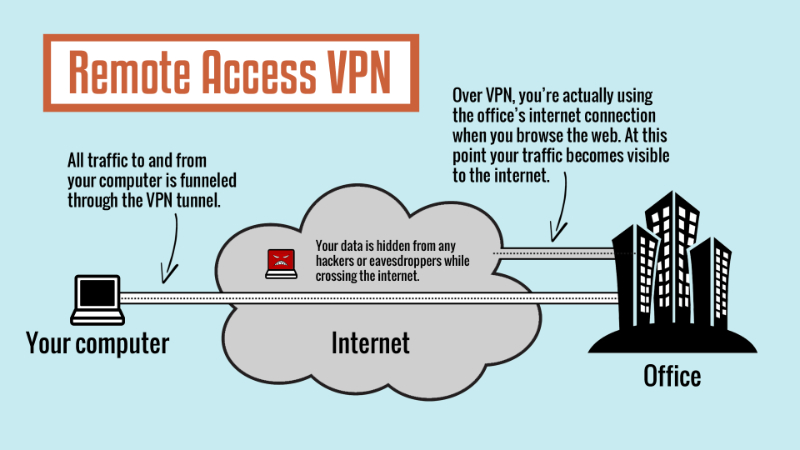
End-node gadgets in the remote area do not require VPN clients because the entrance handles the connection. Many site-to-site VPNs connecting online use IPsec. It is also typical for them to use carrier Multiprotocol Label Switching (MPLS) connections instead of the public web as the transport for site-to-site VPNs.
What Is A Vpn? How Does It Work And Why Do You Need ...

resource that talks about what vpns are
In a mobile VPN, the server still sits at the edge of the company's network, making it possible for safe and secure tunneled gain access to by authenticated, licensed customers. Mobile VPN tunnels are not tied to physical IP addresses.
Hardware VPNs use a variety of benefits over software-based VPNs. In addition to offering enhanced security, hardware VPNs can provide load balancing for large customer loads. Administration is managed through a web internet browser interface. A hardware VPN is more pricey than a software-based one. Because of the cost, hardware VPNs are more feasible for larger companies.
Paid supplier choices tend to be suggested more frequently than free ones, nevertheless. Some VPNvendors, among numerous, consist of the following: contains a strong collection of security functions with a large collection of servers. Nord, VPN has features such as Tor web browser connections for anonymous web surfing, while preserving a strong stance on customer privacy.
Vpn Connection: What Is It And Why Do You Need One?
It does not use too much in terms of additional features and personal privacy tools. Still, it is usually thought about a great VPN service. is a VPN service with a large and diverse set of distributed servers. It has strong privacy and information practices focused on security and provides additional features such as split tunneling.
VPNs are legal in the United States, however users and companies should examine if they are legal in specific countries. Many VPNs offer exceptionally comparable technologies, so it can be hard to pick which VPN will work best. Paid VPN services tend to be more relied on and include more security features.
Around 2017, internet users in the United States discovered that ISPs could collect and offer their searching history, and net neutrality ended up being a principle residents had to battle for-- and effectively lost. An expense was passed by the U.S. House of Representatives in 2019 to restore net neutrality, but was eventually obstructed by the Senate.
What Is Ssl Vpn?
With this understanding, using VPNs became a more genuine need for individuals.
Extranet-based site-to-site In the context of site-to-site configurations, the terms and are utilized to describe two various use cases. An intranet site-to-site VPN explains a configuration where the websites connected by the VPN belong to the very same organization, whereas an extranet site-to-site VPN joins websites belonging to numerous organizations.
(MPLS) performance blurs the L2-L3 identity. Customer (C) gadgets A gadget that is within a consumer's network and not directly linked to the service supplier's network. C devices are not mindful of the VPN.
Sometimes it is just a demarcation point between supplier and customer responsibility. Other suppliers permit consumers to configure it. Supplier edge device (PE) A device, or set of devices, at the edge of the supplier network that links to client networks through CE gadgets and provides the provider's view of the client website.
Provider gadget (P) A device that runs inside the company's core network and does not straight user interface to any customer endpoint. It might, for example, supply routing for lots of provider-operated tunnels that come from various customers' PPVPNs. While the P device is a crucial part of executing PPVPNs, it is not itself VPN-aware and does not keep VPN state.
What Is Vpn? - Understanding Virtual Private Networks
1q LAN trunking to run over transportations such as City Ethernet. As utilized in this context, a VPLS is a Layer 2 PPVPN, imitating the complete functionality of a traditional LAN. From a user viewpoint, a VPLS makes it possible to adjoin a number of LAN sectors over a packet-switched, or optical, company core, a core transparent to the user, making the remote LAN sections act as one single LAN.
PW is similar to VPLS, but it can offer various L2 protocols at both ends. Usually, its user interface is a WAN procedure such as Asynchronous Transfer Mode or Frame Relay. On the other hand, when aiming to offer the appearance of a LAN contiguous between two or more places, the Virtual Private LAN service or IPLS would be suitable.
This section goes over the main architectures for PPVPNs, one where the PE disambiguates duplicate addresses in a single routing instance, and the other, virtual router, in which the PE contains a virtual router circumstances per VPN. The previous method, and its versions, have gained the most attention. One of the difficulties of PPVPNs involves various consumers utilizing the exact same address space, particularly the IPv4 private address space.
Vpn Full Form
A restriction of standard VPNs is that they are point-to-point connections and do not tend to support broadcast domains; for that reason, communication, software, and networking, which are based on layer 2 and broadcast packages, such as Internet, BIOS utilized in Windows networking, may not be fully supported as on a local area network. A VPN does not make one's Web "private". A VPN can log the user's traffic, however this depends on the VPN company. A VPN does not make the user immune to hackers.
Before we dive directly into the inner operations of a VPN, it is a great concept to familiarize yourself with the essentials of what a VPN is and what it does. The acronym VPN means Virtual Private Network. As the name implies, it offers users with a virtual network that is personal so that they can link to the web in a manner that is safe and protected.
We extremely recommend you read this article for a more extensive explanation of a what a VPN is before you read this one, however here's a short primer in any case. How precisely does a VPN do that? A VPN works by routing your device's web connection through your picked VPN's personal server rather than your internet service company (ISP) so that when your information is sent to the web, it comes from the VPN rather than your computer system.
Vpn - Definition By Acronymfinder
This means that your information is transformed into an unreadable code as it takes a trip between your computer and the server of the VPN.Your gadget is now viewed as being on the same regional network as your VPN. Your IP address will in fact be the IP address of one of your VPN Company's servers.
It utilizes an application that produces an encrypted connection to the personal network that you can then use to link to the internet at large. Some VPNs work as a browser add-on. There are a myriad of add-ons you can set up to browsers like Google Chrome or Firefox, while Opera features a built-in VPN.
This is ideal if you have a number of devices you wish to protect as it will safeguard every device connected to the router, conserving you having to install the VPN separately. Additionally, you'll only need to check in as soon as; your router will constantly be connected to your VPN.Connecting your router to a VPN isn't as challenging as you may think.
What Is A Vpn? An Introduction To Virtual Private Networks
The most convenient type of router to get is one that is developed to support VPNs right now, without you needing to do anything more technical that entering your VPN details. These routers can be somewhat more pricey than regular routers, but the convenience is worth it. Organizations often utilize a remote-access VPN for staff members who work from another location.
This is a custom-created service that requires personalized advancement and heavy IT resources. We've gone over how a VPN works and some different ways to execute a VPN, but why exactly should you utilize a VPN? Many people will probably concur that the standard tenets of a VPN are an advantage.
That stated, many individuals postpone getting a VPN, considering it inessential or, worse, unnecessary. They should not. An excellent way of highlighting the requirement of a VPN is to reveal just how exposed you are when your internet connection is not secured. From shopping and paying costs to banking, a lot of daily acts are rapidly moving online.
What Does Vpn Stand For? Are You Using Vpn? You Should ...
By not utilizing a VPN, you're not quite shouting your most delicate information from the roofs, however it is a little like leaving your front door open with your personal info easily set out on a table right inside the door. Possibly you have good, sincere next-door neighbors that won't be available in and take what is important.
Table of Contents
- – What Is A Vpn & How Does It Work?
- – A Guide To Vpn: What Is Virtual Private Networ...
- – [Solved] What Does Vpn Stands For?
- – What Is A Vpn? How Does It Work And Why Do Yo...
- – Vpn Connection: What Is It And Why Do You Nee...
- – What Is Ssl Vpn?
- – What Is Vpn? - Understanding Virtual Private...
- – Vpn Full Form
- – Vpn - Definition By Acronymfinder
- – What Is A Vpn? An Introduction To Virtual Pr...
- – What Does Vpn Stand For? Are You Using Vpn? ...
Latest Posts
9 Best Vpns For Home And Business In 2022
Best Vpn For Business
The Best Vpns For Small And Home-based Businesses
More
Latest Posts
9 Best Vpns For Home And Business In 2022
Best Vpn For Business
The Best Vpns For Small And Home-based Businesses